Try Default

See how revenue teams automate revenue operations with Default.

Key Takeaways
- The “Invalid Cross Reference ID” error means Salesforce can’t map a record ID to a valid, accessible object—often due to sandbox mismatches, schema violations, or deleted references.
- It most commonly occurs in Flows, Apex logic, third-party integrations, and data imports, where object IDs are passed dynamically across contexts.
- Causes include: hardcoded or stale IDs, object type mismatches, missing permissions, or cross-org misalignment.
- You can quickly identify and resolve this using tools like Salesforce Inspector, Workbench, and by decoding ID prefixes to match object expectations.
Your lead routing just broke. Again. But this time, it’s not a logic error or a missing field. It’s Salesforce quietly rejecting an ID it should recognize—grinding automations to a halt with no clear explanation.
The culprit?
“Invalid Cross Reference ID”- a deceptively vague error that strikes when Salesforce can’t resolve a record ID to a valid, accessible object. It’s one of the most disruptive (and poorly explained) blockers in automation, RevOps, and integration pipelines.
In this guide, you’ll learn:
- What causes the error (and how it works under the hood)
- Where it shows up most often (Flows, Apex, integrations, data imports)
- How to fix it using Salesforce-native tools like Inspector and Workbench
- Prevention strategies used by top RevOps and engineering teams
Let’s unpack the error—and eliminate it at the root.
What does “Invalid Cross Reference ID” mean in Salesforce?
Salesforce’s “Invalid Cross Reference ID” error occurs when an object ID is passed into a field, API call, or operation, but Salesforce can’t resolve it to a valid, reachable record. The ID might be well-formed, but it fails resolution because of one of three core problems:
- It belongs to a different org (e.g., sandbox vs. production)
- It points to a record that’s been deleted or isn’t visible to the running context
- It’s an ID for the wrong object type (e.g., a Contact ID used in an Account lookup field)
Internally, Salesforce validates IDs by checking their prefix, record existence, and contextual accessibility (like user permissions or system context). If any of those checks fail, the platform throws this error—often during runtime, when it’s hardest to trace.
Top causes of the “Invalid Cross Reference ID” error in Salesforce
Below are the most common root causes, broken down by failure mode:
Sandbox vs. production ID mismatch
Salesforce record IDs are org-specific—an ID generated in a sandbox won’t resolve in production, and vice versa. This often happens when:
- Flows or Apex code reference hardcoded sandbox IDs
- Test data or metadata is migrated without dynamic lookup logic
- External tools inject IDs from staging into live environments
Even visually identical IDs won’t resolve cross-org unless they point to actual records in the target environment.
Referencing a deleted or archived record
If a referenced record was deleted (or soft-deleted), any lookup, automation, or Apex process pointing to that record will fail.
This is common in:
- Post-deletion automation chains
- Integrations that sync slower than upstream deletes
- Flows assuming records exist after conditional logic branches
Wrong object type for the field
Every Salesforce ID starts with a 3-character prefix tied to its object type (e.g., 003 = Contact, 001 = Account). If you pass an ID with a mismatched prefix into a lookup or relationship field expecting a different object type, Salesforce will reject it—even if the ID exists.
For example: referencing a 003 (Contact) ID in an Account lookup will throw this error.
Insufficient access or visibility
Even if the ID exists, the process executing the operation must have:
- Object-level access (via profile or permission set)
- Field-level visibility to the field containing the reference
- The right execution context (e.g., Flow “Run As” mode or Apex sharing rules)
If any of these are missing, Salesforce may treat a valid ID as invalid.
Malformed or misrouted IDs from integrations
Third-party tools (e.g., web forms, enrichment platforms, ETL pipelines) may push IDs into Salesforce that are:
- Truncated (missing characters)
- Incorrectly formatted (e.g., 15-char vs. 18-char mismatch)
- Pulled from the wrong environment or schema
- Delayed, stale, or no longer present in the target org
Integrations lacking schema enforcement or org awareness are especially vulnerable to this type of error.
When and where Salesforce shows the Invalid Cross Reference ID error
The “Invalid Cross Reference ID” error often appears in high-velocity parts of your Salesforce stack—especially where object IDs are passed between systems, flows, or custom logic without strict validation. Below are the most common breakpoints, broken down by context.
In flows and automation rules (admin)
Admins frequently hit this error when using Flow Builder, Process Builder, or workflow rules that reference:
- Newly created records in the same flow before they've committed to the database
- Hardcoded IDs copied from sandbox or export tools
- Record variables that are null, blank, or conditionally populated
If a referenced variable hasn’t been assigned, Salesforce passes an empty value—triggering a runtime resolution failure.
In Apex code (developer)
Apex code surfaces this error when:
- IDs are passed into methods or DML statements without object-type validation
- Relationships are assigned using raw strings instead of properly typed references
- DML operations try to insert/update objects that rely on invalid or deleted related records
In bulk operations, a single bad ID can cause the entire transaction to fail unless exception handling is in place.
In third-party integrations
Integrations—especially those pushing data in real time—commonly trigger this error due to:
- Sandbox-to-production leakage (misrouted IDs)
- Delayed syncs referencing deleted or moved records
- Tools like Zapier, Clearbit, or Marketo that send IDs without schema validation
If the external system assumes the ID is valid, but Salesforce can’t resolve it, the call will fail—sometimes silently.
In data imports and ETL pipelines
Data import jobs (via Data Loader, Hightouch, Segment, etc.) often fail when:
- Upserts are run using outdated IDs from a previous export
- Lookup fields are populated without prefix validation
- Cross-object updates assume matching schema without fallbacks
Large-volume imports can mask this error until deep into the pipeline, especially when IDs are reused across environments.
Error scenarios by context
How to fix the Invalid Cross Reference ID error in Salesforce (step-by-step)
To resolve this error, you need to isolate whether the object ID in question is:
- Well-formed (correct format and length)
- From the correct org and object type
- Accessible in the current execution context
Here’s how to systematically validate each layer:
Use Salesforce Inspector to validate the ID
Start with a fast ID check. Salesforce Inspector is a Chrome extension that lets you instantly inspect and query record IDs directly from the UI. It’s a go-to tool for admins and developers debugging Flows, automations, or Apex interactions.
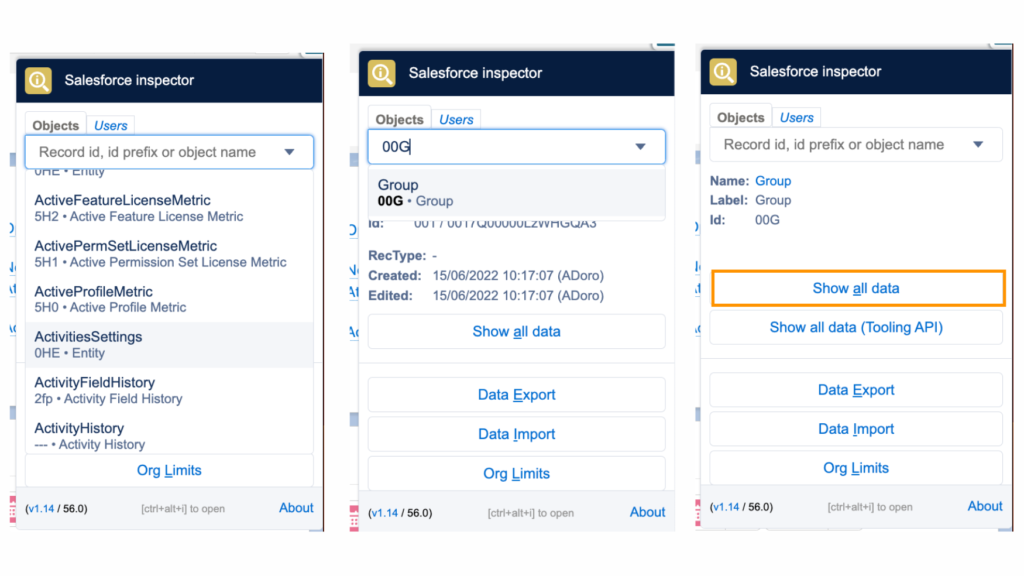
Source: Salesforce Ben
Steps:
- Open any Salesforce record → click the extension
- Use “Show all data” or “Query Editor” to test the suspected ID
- If no data returns: the ID is invalid, inaccessible, or from another org
This is ideal for quick, inline validation—especially during Flow or automation debugging.
Decode the ID prefix to identify the object type
Salesforce IDs are structured. The first three characters—called the prefix—indicate the object type (e.g., Account, Contact, Lead). Comparing the prefix against the expected object type often surfaces silent mismatches early.
- 001 = Account
- 003 = Contact
- 500 = Case
- 00Q = Lead
- 006 = Opportunity
Compare the prefix of your ID to the field or relationship type it’s being used in. If there’s a mismatch, you’ve found the error.
Use a prefix reference chart or this community list to debug custom object types as well.
Use Workbench to confirm existence + permissions
If you suspect an ID is valid but inaccessible, Workbench helps confirm whether the record exists and if your current session has permission to access it. It’s useful for deeper debugging, especially in sandbox vs. production scenarios.
- Go to Workbench
- Login → navigate to “SOQL Query”
- Run your query using the suspected ID
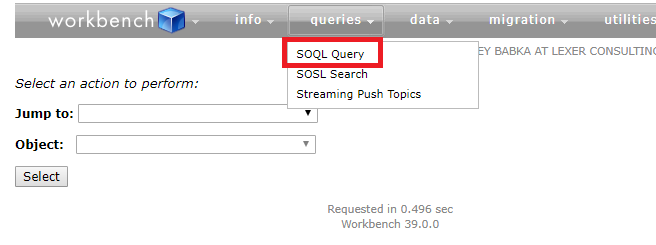
Source: Marksgroup
If the query fails:
- The record may be deleted
- The object type may not match
- Your session lacks access to that object
Top Tip: Switch between “Standard” and “System Admin” sessions to test access scopes.
Check visibility and execution context
Even a valid, existing ID can trigger this error if the automation or code lacks the right access context. Visibility depends on user permissions, Flow context settings, and Apex sharing behavior.
Checks to perform:
- In Flows: Check “Run As” settings (System vs. User context)
- In Apex: Ensure the class uses with sharing or explicitly handles access via Schema.sObjectType checks
- Use Field Accessibility reports to confirm visibility at the profile level
Many failures stem from record-level sharing rules that restrict visibility during runtime—even when the ID is technically correct.
For integrations: log and retry with fallback
When integrations like webhooks, enrichment tools, or lead capture forms pass IDs into Salesforce, they often bypass object validation. Adding pre-checks and fallback logic prevents brittle errors from breaking syncs or workflows.
Steps:
- Add logging + retry logic to capture malformed or unmapped IDs
- Validate incoming IDs against the Salesforce object schema (prefix or record existence) before DML
- Consider using middleware (e.g., Tray.io, Workato) to sanitize and route based on org-aware logic
How to prevent the Invalid Cross Reference ID error in Salesforce
Preventing “Invalid Cross Reference ID” errors requires more than patching failures—it’s about building systems that assume IDs can be malformed, out-of-scope, or out-of-date. Here’s how experienced RevOps and engineering teams design proactively to eliminate these errors at scale.
Validate IDs early in Flows and Apex
Don’t wait until runtime to check if an ID is valid—catch issues upstream. Validating IDs before they’re used in logic or DML ensures that automation only references well-formed, accessible records.
Use decision elements or isBlank() checks in Flow to verify that an ID exists before referencing it downstream. In Apex, validate ID length (15 or 18 chars), prefix, and object compatibility before assignment or DML.
Pro Tip: Use Id.valueOf(id).getSObjectType() to dynamically validate type in Apex logic.
Avoid hardcoded or environment-specific IDs
Hardcoded record IDs are one of the top sources of this error, especially when copied from sandbox environments. Instead of hardcoding, use dynamic references that adapt across environments.
Never hardcode record IDs—especially from sandbox or staging. Instead:
- Use Custom Metadata Types to store references safely across orgs
- Reference records by Name or Unique External ID with a SOQL fallback
- For Flows, use Get Records steps instead of static resource variables
Even test classes should avoid hardcoded IDs by dynamically creating records in setup.
Implement error handling and guardrails
Errors will happen, but they don’t have to break your entire process. Add structured fault handling, logging, and alerts to make invalid ID usage visible and recoverable.
In any context that touches object relationships (lookups, cross-object logic, etc.):
- Wrap DML in try/catch blocks and log failed record IDs
- Use Fault paths in Flows to route errors to alerts or logs
- Add integration validation layers to sanitize incoming records before insert/update
Defensive handling doesn’t just fail gracefully—it helps identify systemic patterns early.
Align automation context with access requirements
Your automation is only as powerful as the context it runs in. Make sure Flows and Apex code have the right visibility and sharing behavior to access referenced records.
Ensure your automations run in the appropriate context:
- For Flows: use System Context with Access Checks when security matters
- In Apex: choose with sharing or without sharing deliberately, based on access needs
- Periodically audit which users or profiles trigger which automation layers
Quarterly audits using Field Accessibility reports or Security Health Check help prevent silent breakages as orgs evolve.
Common prevention patterns
Automatically prevent ID errors in Salesforce with Default
You can follow every best practice. Validate your IDs. Guard every automation path. But if just one invalid reference slips through, your routing breaks, your syncs fail, and your GTM momentum stalls.
Default stops that from happening.
With Default’s inbound orchestration platform, RevOps teams can:
- Pre-validate every ID before it hits Salesforce—so no more sandbox leakage or stale references
- Automatically enforce object-type and org-aware logic—without brittle hardcoded rules
- Log, flag, and reroute failures instantly—to Slack, CRM, or a safe fallback
- Build lead flows that self-heal from schema shifts, permission gaps, or hidden visibility issues
Instead of chasing cross-reference errors after the fact, Default ensures broken IDs never reach your pipeline in the first place.
Ready to stop firefighting and start flowing?Explore how Default keeps your GTM ops clean and error-free: Book your free interactive demo today.
Salesforce Invalid Cross-Reference ID FAQ
Is "invalid cross reference id" the same as "malformed ID"?
No. A Malformed ID fails basic validation—it’s the wrong length (not 15 or 18 characters), contains invalid characters, or isn’t a Salesforce ID at all.
An Invalid Cross Reference ID, on the other hand, is syntactically correct but fails because it’s pointing to the wrong object, a deleted record, or one that’s inaccessible in context.
How do ID prefixes help identify invalid references?
Salesforce ID prefixes indicate the object type. For example:
- 001 → Account
- 003 → Contact
- 00Q → Lead
If you pass a Contact ID into a field expecting an Account, Salesforce throws this error, even if the record exists. Prefix checking is a fast way to catch type mismatches early in Apex or Flow logic.
Does this affect only lookup fields?
No. While lookup fields are a common trigger, this error can also occur in:
- Apex assignments to relationship fields
- Flow inputs where IDs are dynamically passed
- Upsert or merge operations using external data
- Integrations that inject invalid IDs into mapped fields
Anywhere Salesforce expects a valid ID, this error can surface, even outside of lookup UI elements.
Conclusion

Former pro Olympic athlete turned growth marketer. Previously worked at Chili Piper and co-founded my own company before joining Default two years ago.
Run revenue as an engineered system
Revamp inbound with easier routing, actionable intent, and faster scheduling












.png)